Conditional Access provides the most fine-grained control when you’re managing the multi-factor authentication requirements for your organization. Conditional Access policies can be configured from the Azure portal.
To access the Conditional Access configuration page, follow these steps:
- Navigate to the Azure portal (https://portal.azure.com).
- Select Azure Active Directory | Security | Conditional Access, and then choose Policies.
You can create new policies or use one of the Microsoft-provided sample Conditional Access policy templates (14 in total). Policies created via templates can be modified once they have been deployed to your tenant.
To configure a template-based policy, follow these steps: - From the Conditional Access | Policies page, select New policy from template (Preview):
Figure 8.35 – Creating a new Conditional Access policy from a template
- Select one of the templates, such as Require multifactor authentication for all users, and click Next: Review + create:
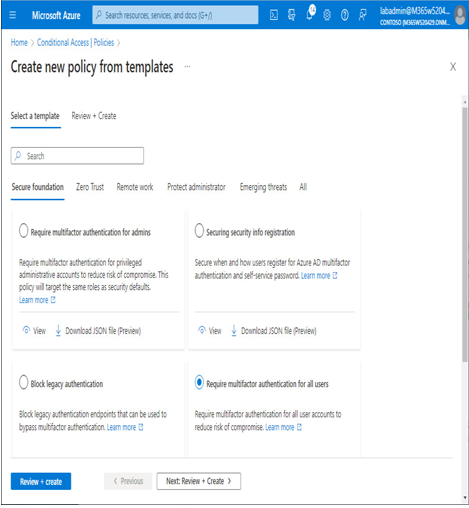
Figure 8.36 – Selecting a template
- Review the settings and click Create.
Policies created through templates cannot be modified during creation, except via enforcement mode. All template-based policies are configured in Report only mode, which can be toggled during creation. The user creating the policy is excluded from the policy to prevent accidental lock-out.
Once the template policies have been configured, you can edit the scope and conditions for the policy – for example, a manually-created policy.
FURTHER READING
For more information on Conditional Access templates, see https://learn.microsoft.com/en-us/azure/active-directory/conditional-access/concept-conditional-access-policy-common.
Summary
In this chapter, you learned about Azure AD Identity Governance and Identity Protection features. Access packages can be used as part of Identity Governance to help you manage the life cycle of resource access, including granting roles and access to SharePoint sites, Teams, and Groups. You can also use access reviews to periodically audit things such as application access or group membership. You also learned about Identity Protection features, such as risk-based access policies, and how to investigate and remediate risks.
In the next chapter, we’ll learn how to configure application access.
Knowledge check
In this section, we’ll test your knowledge of some key elements from this chapter.